By: Basel Khaled
New research from F5 Labs shows that the spread of Thingbots continues unabated and that they are being developed by everyone from children to sophisticated nation states.
The sixth volume of The Hunt for IoT1 report notes that 26 Thingbots2, which can be co-opted by hackers to become part of a botnet of networked things, were discovered and/or reported on between October 2018 and January 2019. Six were discovered in the entirety of 2017 and nine in 2016.
“The number of IoT threats will continue to rise until customers demand more secure development strategies for manufacturing devices,” said Sara Boddy, F5 Labs Research Director.
“Unfortunately, the process hasn’t yet begun. It will be several years before we see a noticeable impact from new, secure IoT devices reducing the threat surface. At the same time, everyone from script kiddies to nation-states will continue to compromise IoT devices.”
When F5 Labs tested IoT devices used in mission critical deployments, such as providing internet service to emergency fleets, 62% of were deemed vulnerable. Theoretically, critical systems would be secured better than a non-critical system.
According to Gartner, there will be more than 20 billion IoT devices in circulation by next year3. Extrapolating F5 Labs’ 62% figure means a threat surface of at least 12 billion IoT devices that could be compromised and used for attacks.
Meanwhile, analysis from DBS Bank indicates that 100% market adoption will take place in the next ten years4. 2019 is seen as the tipping point between first adopters and the early majority, where sales and deployment of IoT devices take off at an exponential rate.
Mirai’s enduring legacy and Europe in the firing-line
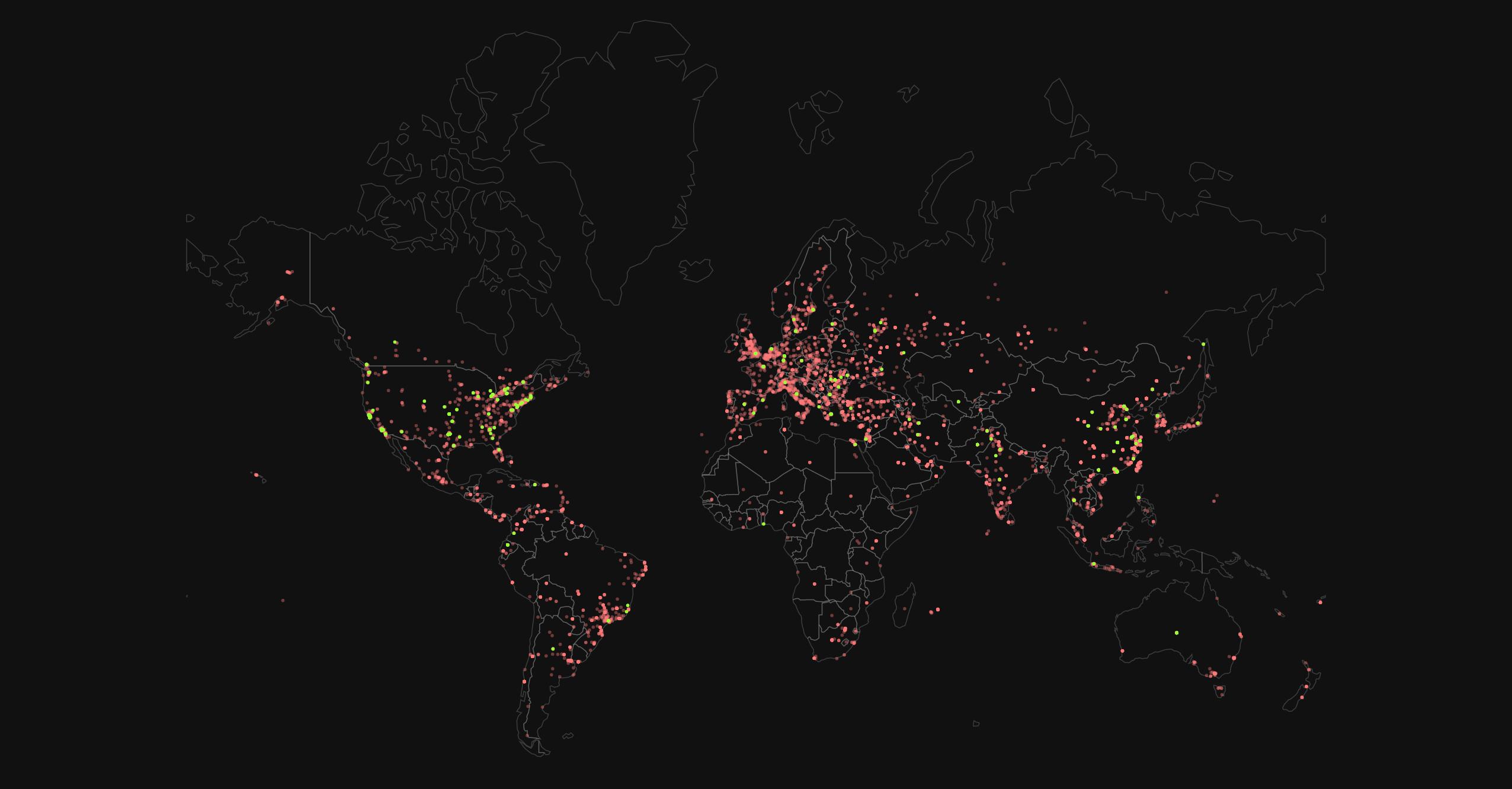
Mirai – the most powerful Thingbot yet to have launched an attack – still casts a long and influential shadow, partly due to a distributed scanning model that enable self-reproduction.
Europe has been the most vulnerable to future attacks since June 2017, with data from F5 Labs partner Baffin Bay Networks indicating the region has more Mirai scanners – compromised IoT devices seeking to spread infection – than anywhere else in the world5.
Not only is the threat of the original Mirai bot still powerfully present, but there are also a multitude of offshoots to consider.
88% of all known Thingbots have been discovered post-Mirai launch, largely driven by publicity and its source code availability. 46% of those new discoveries are Mirai variants, many of which are capable of much more than launching DDoS attacks, including deploying proxy servers, mining crypto-currencies and installing other bots. Other key Hunt for IoT report observations included:
• Device types. Small office/home office (SOHO) routers, IP cameras, DVR, NVR, and CCTVs remain the primary IoT device type compromised by Thingbots. Infections are considered use-case based rather than attackers targeting IoT devices for specific attack purposes. The sheer volume of publicly accessible devices means they will always stay in attacker’s crosshairs. They are also a target of researchers looking for IoT vulnerabilities, which are often subsequently exploited by bad actors controlling botnets.
• Shifting attack methods. Thingbots are increasingly targeting IoT devices using HTTP, and publicly exposed UPnP, HNAP and SSH (services that should not be exposed publicly). A full 30% of the new thingbot discoveries target IoT devices through Common Vulnerabilities and Exposures (CVE).
• Cheap attacks and endless possibilities. Once malware is installed on an IoT device, the bot will contact the C&C server and download its orders (DDos attacks in most cases). In addition, these Thingbots are deploying proxy servers to use for launching attacks, collecting information from traffic traversing devices, encrypting traffic, mining cryptocurrencies, and launching web application attacks. Notably, the sale of botnet services has moved from the shadows of darkweb forums to mainstream platforms like Instagram, a move in line with the rise of “script-kiddie gamer” personas building and selling IoT botnets. Subscription plans for botnet services go for as little as $5 a month.
• Lack of detail. Details are missing for many newly discovered Thingbots. The good news is that the security community is discovering bots before they attack. In the past, the majority of Thingbots were discovered through investigating attack traffic, uncovering the bot as well as attack types and infected devices. The fact that we’re discovering bots before they launch is a positive. However, the security community is still several steps behind attackers due to laws prohibiting unauthorized access to a system. To truly understand attacker behaviour, we need to get on the devices they infect. Legislation has been proposed in the US for ethical researchers to get a “hall pass,”. However, there are still instances of ethical researchers getting charged with computer intrusion crimes.
“Waiting on IoT manufacturers to offer secure products or trusting implementers to effectively deploy security controls on IoT devices is a waste of time. Why think IoT would be any different than standard IT, which already struggles? Businesses getting hit by IoT bot attacks must buckle up and defend themselves,” added Boddy.
“Start with the most common attacks launched by Thingbots: DDoS and web application attacks. For DDoS attacks, a cloud scrubbing provider is the way to go, mainly because attack sizes beyond the capacity of most networks – outside service providers and large banks – only cost $20 to launch. Then there’s web application attacks, which now require web application firewalls with behaviour-based bot detection and traffic blocking. Never cut corners with your IoT homework. Don’t buy products with known vulnerabilities, obvious exploit histories or substandard security mechanisms. Always quarantine or retire any devices that cannot be secured.”